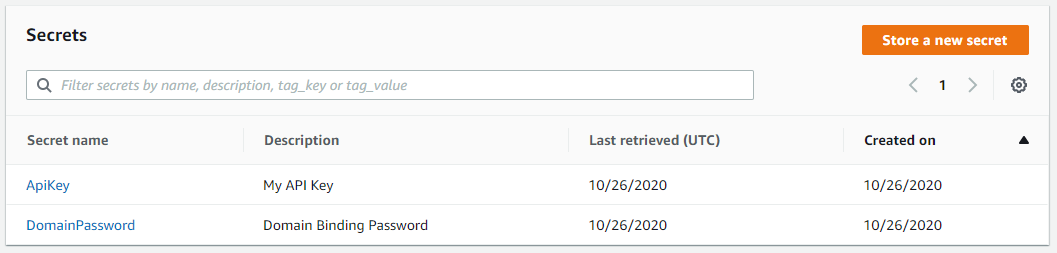
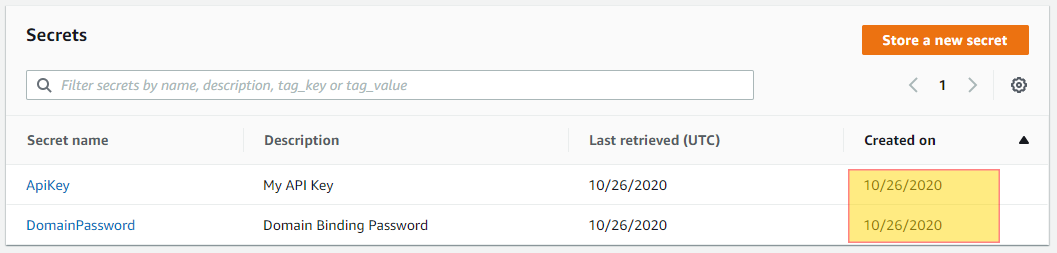
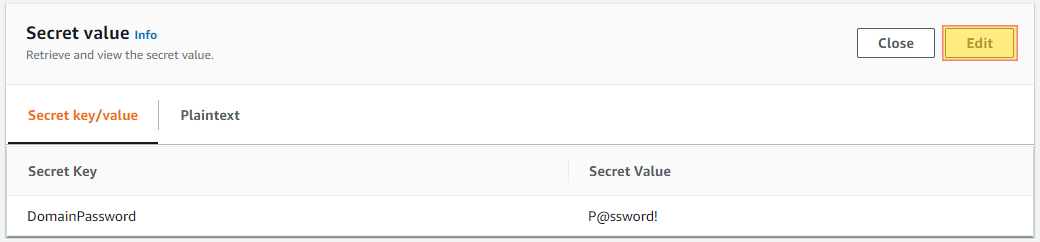
Ensure that you are rotating your secretes every 90 days. Secrets should be treated just as passwords and should have a particular rotation cycle that follows similar to your service account password policy. This is considered a security best practice and should always be done. Ensuring this is enabled will help with NIST and PCI-DSS compliance.
Do you want to see all S3 Buckets in once place for all regions and all accounts?
Login to our online demo to see exactly what this looks like.
demo.intelligentdiscovery.io
Consolidate your inventory management with consistent and frequent security logs, inventories, and change logs. Dashboard reporting for extensive analytical value.
learn more +Access consolidated capacity, cost, and volume tools in a scaling environment without impacting production or breaking the bank.
learn more +