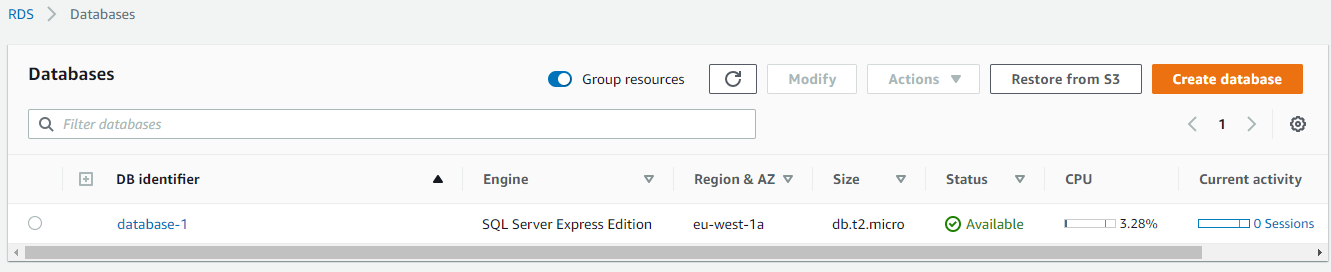
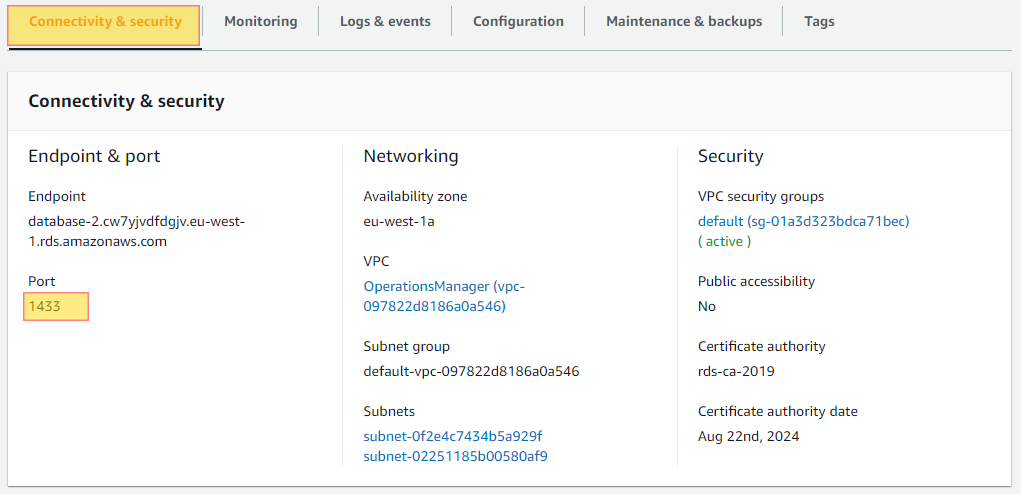
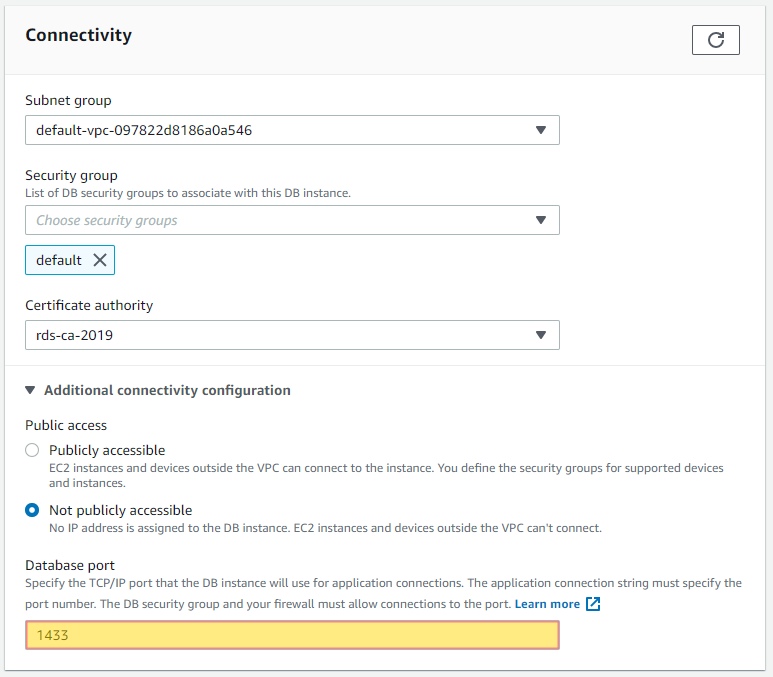
Ensure that your RDS database instances have specified another port to use other than there default port. This will help limit attacks against your database as understanding what port is open can give a hacker insight into what database you are running and craft and exploit directly targeting that specific database engine. This is why this is considered a security best practice and should be enabled. Ensuring this is enabled will help with NIST compliance.
Do you want to see all of your RDS Instances in once place for all regions and all accounts?
Login to our online demo to see exactly what this looks like.
demo.intelligentdiscovery.io
Consolidate your inventory management with consistent and frequent security logs, inventories, and change logs. Dashboard reporting for extensive analytical value.
learn more +Access consolidated capacity, cost, and volume tools in a scaling environment without impacting production or breaking the bank.
learn more +