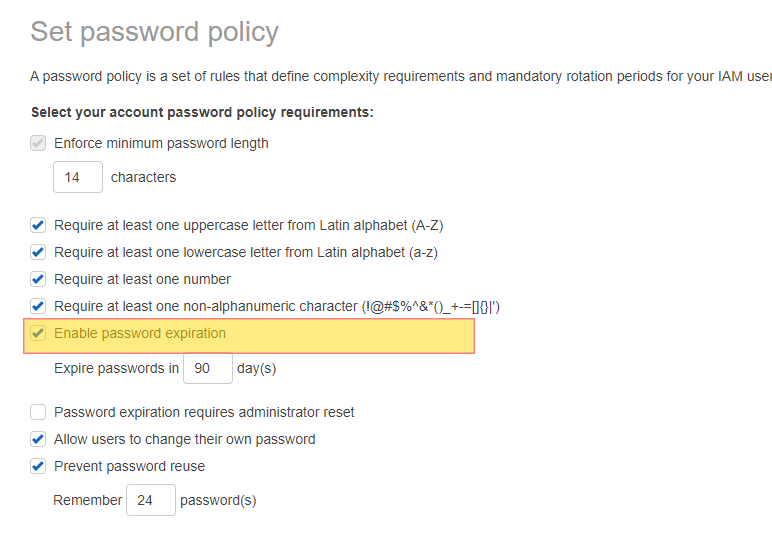
IAM allows for creating users directly with in the AWS console for end users to be allowed to interact with the various services that AWS offers. Password policies should follow that of what industry standards state for the enterprise, ensure password is changed at least once every 90 days. For this reason it is considered a security best practice not keep using the same password. Ensuring that it is restricted will help you with CIS and NIST Compliance.
Do you want to see all of your AWS EC2 Instances in once place for all regions and all accounts?
Login to our online demo to see exactly what this looks like.
demo.intelligentdiscovery.io
Consolidate your inventory management with consistent and frequent security logs, inventories, and change logs. Dashboard reporting for extensive analytical value.
learn more +Access consolidated capacity, cost, and volume tools in a scaling environment without impacting production or breaking the bank.
learn more +